Code Signing Certificates FAQS
Get All the Answers About Code Signing Certificate Related Issues & Errors
It is prerequisite security certificate for any software publisher or software developer who produce software code or script and publish them on the Internet.
Code Signing Certificate enhance the factor of trust and confidence towards online software publishers and helps them to establish the reputation while delivering the software code or script to online users.
Yes, Comodo Code Signing Certificate offers an individual code signing certificate to freelance web developers or software publisher who wants to build trusted relationship with online audiences.
Code Signing Digital Certificate authenticate the name of real publisher and assures the integrity of software before publishing it on the Internet.
Yes, it is one of the key factor when it comes to software integrity and legitimacy of an original software manufacturer. It builds the bridge of trust and confidence between software publishers and audiences.
EV Code Signing Certificate is the modern digital signature for enterprise or wide-scale online software publishers. As per CA/Browser forum and Microsoft's specifications, it can be issued only after the validation of online organization and it require the private key in the form of hardware token and the PIN number to authenticate an integrity of software code.
Per CA/Browser norms, all Certificate Authority Issues Code Signing Certificate with the validity of two or three year only.
You can protect as many as application through a single Code Signing Certificate. Comodo CA allows unlimited applications security with one code signing certificate.
The validation of Code Signing Certificate requires some legal documents that you need to provide to Certificate Authority to get validate your online organization. We build the streamlined guide for the validation process which will help you to make the process faster. Read more about Code Signing Certificate Requirements.
Authenticode (Code Signing) is not a guarantee that the software that has been digitally signed is bug free or even virus/malware free. All a digital signature says is “this file has not been modified since it was signed by the publisher”. Having said that it is worth noting that obtaining a code signing certificate is not free and that companies or individuals that apply for a code signing certificate do have to pay a fee and do have to prove their identity to the company that issues the certificate.
Anyone, really!
However, keep in mind that code signing certificates can only be issued to "legal entities", like registered companies or directly to individuals (in the latter case, your name is used as the Publisher). A code signing certificate is an identity verification product so the "publisher" needs to be a recognized business.
You can get a code signing certificate even if your business is just you "Doing Business As" another name, as long as that name has been registered and is recognized by other 3rd parties (like banks, utility companies, phone companies, etc). Normally officially filing a DBA (Doing Business As) name is very easy to do with your local or State government.
You cannot get a code signing certificate with the name of your website as the publisher unless you have registered your website as your business name (like Amazon.com).
See the FAQ entry for "Validation Requirements" for a full list of documentation that Comodo might ask you for.
Unfortunately, no, by necessity there can't be a free trial because every order has to pass through validation where the identity of the publisher ordering is verified.
We do, however, offer a 100% money-back guarantee. If you don't want or need the certificate after you order it you can always get your money back.
The order process consists of two steps, placing the order (filling out a short form at https://codesigncert.com) and validating your identity with Comodo. The validation process is handled via email by Comodo and you will receive full instructions with your order confirmation within a few minutes. Follow those instructions and you'll receive a link to collect your certificate and install it into your browser then you export the code signing certificate to a PFX/P12 file and use that file with a signing utility (like kSign). It is important that you use the same computer and browser to order and collect the certificate but after collection the certificate can be exported and used on any number of computers or servers.
For export instructions please see the FAQ entries for "How do I export my certificate to a file.." -- the process varies depending on which browser is used so be sure you follow the instructions for the browser you used to order.
We recommend you use Internet Explorer or Firefox to order but mobile browsers are not supported in the ordering process.
Code signing certificates are valid from 1 to 5 years. When your certificate expires only your ability to create new signatures is affected, past signatures remain valid as long as you used a timestamp when you sign.
Comodo provides a timestamp server free to any certificate holder, the URL is https://timestamp.comodoca.com/authenticode - that URL can be passed to signing utilities like Microsoft's signtool.exe. You should always use a timestamp!
How long does it take to get a Code Signing Certificate?
Assuming you have all of the documentation required ready to send over the entire process generally takes no more than 2 business days. For more information about the documentation requirements see the FAQ (or just drop us a line).
Put simply, a timestamp records when a signature was created. Because all code signing certificates expire it is important for any software verifying a digital signature to know if the signature was created before or after the certificate expires. If you use a timestamp your signatures never expire, even when your certificate does.
It signs but other code signing utilities like Microsoft's signtool.exe need to be passed a URL for a timestamp server. Comodo offers a timestamp server for free for any certificate holder, the URL is https://timestamp.comodoca.com/authenticode
For Microsoft's SignTool (4.0 and later) and others applications like Jarsigner which support RFC 3161 (Time Stamping Protocol): use the URL https://timestamp.comodoca.com/authenticode
NOTE : For signing macros in MS Office / VBA - use the Authenticode URL (https://timestamp.comodoca.com/authenticode)
The only time a browser comes into the equation is at order and collection time. Users do not need to install the certificate for it to change the Unknown Publisher warnings on your downloads, the certificates are already trusted in all versions of Windows (and OSX, most Java devices, Android and iOS too).
Mobile browsers are not supported for ordering.
When ordering the browser does play a key (yet temporary) role because it creates the CSR (certificate signing request), and generates the private key and stores that key temporarily in your browser. The recommended browser for ordering is Firefox, because it works out of the box and doesn't prompt users unnecessarily with warnings, prompts and options like some other browsers do. However, most other major browsers will work as well.
Generally that means that you are visiting the collection link either in a different browser or on a different computer than the one you used to order. The private key portion of the order is temporarily stored in the browser for security (so that it never leaves your possession) and is paired with the certificate at collection time (so you can export it to a PFX file -- see the Exporting tutorials for instructions there).
The other possible reason you might see an error message like that is if you used Chrome to order. If that is the case,email us with your order number and we'll fix it for you.
In order to use your certificate you need to export it to a file.There are a number of browser-based export tutorials located here. If you're stuck just drop us a line at mailto:support@codesigncert.com and we'll help!
As of late August 2013, all valid (not expired, not revoked) Comodo Code Signing Certificates can be used for Kernel-Mode Code Signing!!! (For Windows Vista and greater)
1. Download the Comodo cross-signed CA that matches your Code Signing certificate's Root CA.
2. Open an elevated Windows command prompt (cmd) and run signtool.exe :
signtool.exe sign /v /ac "CROSS_SIGNED_COMODO_CA_HERE" /f YOUR_PFX_HERE /trhttps://timestamp.comodoca.com/rfc3161 "FULL_PATH_TO_FILE_TO_SIGN"
Example: signtool.exe /v /ac "AddTrustExternalCARoot_kmod.crt" /f my.pfx /trhttps://timestamp.comodoca.com/rfc3161 "C:\myfile.dll"
Note: For most customers CROSS_SIGNED_COMODO_CA_HERE will be:
[KMCS] AddTrust External CA Root
OR
[KMCS] UTN-USERFirst-Object
For more general information and instruction about kernel mode signing certificates, see Microsoft's Kernel-Mode Code Signing Walkthrough . (MSDN.microsoft.com)
YES!
One certificate will sign on ALL supported platforms. Microsoft Authenticode (DLL, EXE, COM, etc), Java, Mozilla, Android, Adobe AIR, Flash, Silverlight,
MS-Office and OSX/iOS.
YES!
That's exactly what they do -- verify a publisher's identity.
Without a code signing certificate your users will see :
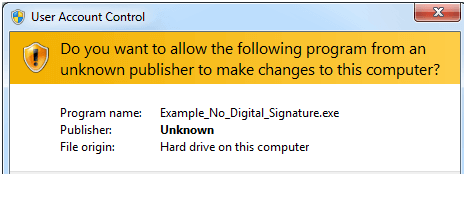
WITH a code signing certificate your users will see :
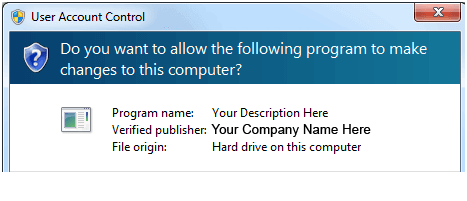
Almost. The "This file may harm your computer" warning is actually generated by a Microsoft software called SmartScreen. SmartScreen uses file reputation
to warn users when a file hasn't been downloaded very often. A digital signature does help SmartScreen identify your files but a signature alone doesn't
instantly mean your users won't see the SmartScreen warning. With a digital signature and some time, that SmartScreen warning will disappear (and stay
gone, as long as you're signing your files so you can always be identified as the publisher).
One trick we've learned is to release some sort of freeware download that is signed with the same digital signature. Users tend to download free software
much more than trial versions or commercial versions so you get the reputation bump (because of the digital signature) on all files you download.
In summary, a digital signature alone won't guarantee your software isn't flagged by SmartScreen but signing helps ensure that your software's reputation
can be recognized for everything you sign. That means that when you release new versions or editions of your software your SmartScreen reputation is
maintained and doesn't have to start from scratch.
.p12 is an alternate extension for what is generally referred to as a "PFX file", it's the combined format that holds the private key and certificate and
is the format most modern signing utilities use. If you have a .p12 file that you exported from Firefox or Safari just rename the .p12 extension to .PFX if
you need to, it's the same format.
If your signing tools refer to a PKCS12 file, that is the same thing as well.
FIPS-140 Level 2 USB or Existing HSM
Stored on an External Physical Device
3 to 5 Business Days
Code Signing Certificate Compatibility Supported by All Major Platforms
Achieve cross-platform compatibility with trusted code signing certificate for secure software and application distribution.
Why Choose CodeSignCert for Code Signing Security Certificates?
24/7 Help Desk
Create your support and sales ticket in minutes, and get support from an expert instantly.
30 Day Money Back Assurance
Get your refund with no question ask policy for your purchase, renewal, or order within 30 days of the initial order date.