Obtain a Code Signing Certificate Security
Over last decade, smart-phone usage has sky-rocketed to an extent of becoming a trend followed by seemingly every person you pass by on a street. Even mobile platforms like Android, iOS, Windows, BlackBerry, etc. are in a race to attract maximum number of users. Most users rely on their smart-phones for social interaction, private conversation, online shopping, e-banking and other similar tasks.
However, with the increase in the use of smart-phones, cyber attackers have upgraded their standard attacks on websites to hijacking or hacking smart-phones to steal users’ identity credentials, phone data and other sensitive information stored in the device. Therefore, it is very important for developers of mobile applications/software to develop more complex and trustworthy applications using digital technology.
After developing applications/software, it is very important to secure their codes and scripts to prevent attackers from tampering the application. To secure code, developers need to use Code Signing certificates, which are offered by trusted certification authorities (CA).
What are Code Signing certificates?
Code Signing certificates enable developers to sign executables and scripts to verify their identities before distributing them on the Internet.This guarantees to the user that the code or the application has not been altered since it was signed by the author using cryptographic hash function.Trusted root CAs sign these certificates using Public Key Infrastructure (PKI).
Why is it important to use Code signing certificates?
It has been found that, when a software or an application is signed using a Code signing certificate, it achieves more downloads on the Internet. The reason being that code signing shows confirms the author’s identity, which users find trustworthy enough to download from the Internet.
Code signing increases users’ trust in following two ways:
- Authenticity – It verifies the author of the software
- Integrity – It verifies that the software or the code has not been tampered after it was signed
Code Signing Certificate Path
Code Signing certificate is verified in following chain of CAs.
- Primary CA
- Code Signing certificate
- Author details
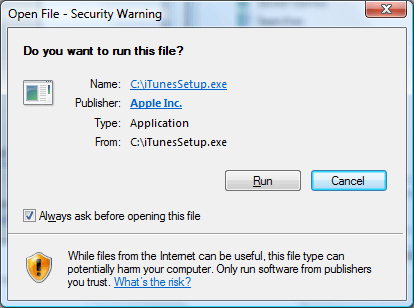
How do I know if the software is trusted?
Users can know the details about the application or software being downloaded by having a look at the warning window generated during the process. On this, the users can find the author’s name and website included, which helps them decide about the authenticity of the application or software.
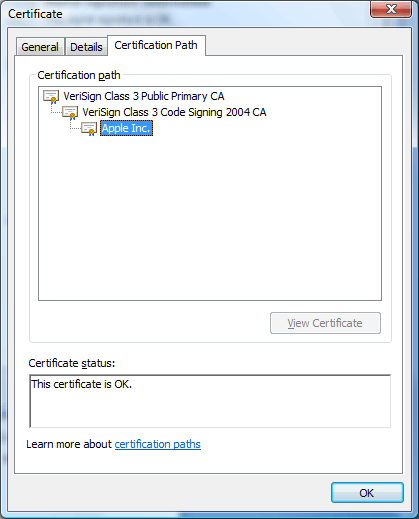
It can be explained with an example of an executable file iTunesSetup.exe.See Figure 2. In the pop-up window, one can find the publisher’s name as Apple Incalong with Apple’sofficial website.
How does a Code Signing certificate work?
To sign a piece of code, the author has to perform following steps:
- Apply for a Code signing certificate via a trusted CA.
- Submit identity details to the CA. The applicant receives the certificate only after authorities verify the identity credentials.
- Generate a one-way hash for the software and use the private key to encrypt this hash.
- Bundle-up the hash and the certificate with the executables.
Verification of the application/ software at the users’ end:
- Decrypting the hash using code signing certificate’s public key
- Create a new hash for the downloaded application.
- And compare the new hash with the hash used for code-signing.
- If both the hashes match perfectly, application is not modified since it was signed. The user is now safe to download it.
Most of the steps mentioned above are handled by the users’ Operating Systems automatically.
Platforms compatible for code signing
Desktop Based Platform
- Microsoft Authenticode [32/64 bit Files (.exe, .dll, .ocx, .cab)]
- Java’s .JAR files and software
- Microsoft’s Office files & VBA documents
- Adobe’s AIR based Applications.
- Apple Os X Software
Mobile Based Platform
- Windows Phone and Xbox 360 applications
- Android Applications
- Apple iOS Applications
- Brew Applications

Software developers and publishers using any of the above mentioned platforms can use Code signing certificates to reduce the unusual error messages or window pop-ups that stops customers to go forward with downloading the application. Absence of such windows boosts users’ confidence in the authenticity of the application.
With Code signing certificates, developers can distribute their codes, applications and software on the Internet. Safe enough for the users to download it without worrying about the author’s identity or the software’s authenticity.
Categories
Latest Post
- TPM vs HSM: Key Differences, Use Cases, Threat Models & Compliance Guide (2025 Edition)
- All You Need to Know About Code Injection: Types, Prevention & Detection Methods
- Microsoft Makes MFA Mandatory for Azure and Microsoft 365 Admin Accounts
- How to Digitally Sign Binaries with Signing Manager Controller (SMCTL)?
- Signing an XML file using Code Signing Certificate - How to Guide?
- Firmware Signing vs. Code Signing: Key Differences and Use Cases
- Firmware Signing Explained: Best Practices for Secure Updates
- Digitally Signing Excel Macro Project Using Code Signing
- How to Configure DigiCert KeyLocker on Windows (Step-by-Step Guide)
- How to Use YubiKey for Mac Code Signing?
Customers Reviews
FIPS-140 Level 2 USB or Existing HSM
Stored on an External Physical Device
3 to 5 Business Days