Why iOS Developers Require Code Signing Certificate
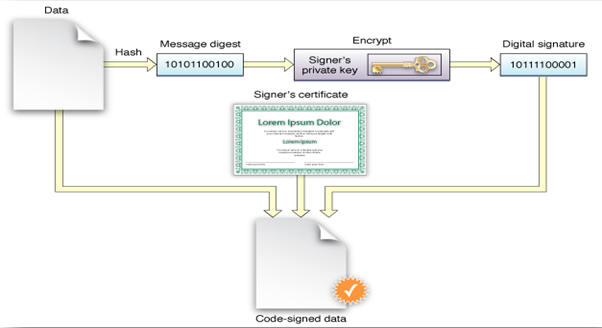
Code signing is a security key and private essential quality that is required in OS X, to certify your app. The properties installed by this code signing is that if you signed in the application once in your system, then the signing certificate should be able to detect the regarding change of the app. This kind of change may occur by malware code or by accidentally. Code signing certificate is basically the form of a digital authentication that justify one’s entry. The code is designed in the manner that it keeps tracking the individual information which is digitally interlinked with that security key.
Internet has become all invasive platforms. With increase in smart phone users, most of the online activities have shifted to devices like phones, tablets or laptops as users rely on these. However, most of the users are plagued with the question whether it is safe to use internet on the phone due to increased accounts of malware and spam attacks. Viewing content on the internet means downloading applications; plug ins, tools, scripts, macros and more forms of data, any of which could be malicious.
The computer giant Microsoft has presented an innovative solution to this problem by introducing the concept of code signing and certification with the help of modern digital signature technology. Code signing has been defined as a technique used by software developers to digitally sign the downloadable codes they provide for the purpose of providing the credibility of the code. People, using Apple devices are not be able to operate unauthorized programs in that. The iOS system is extremely efficient at detecting alliance to trusted certificate vendors like Thawte Code Signing Certificate. While Symantec Code Signing Certificate is reasonably priced and comes with great features like unlimited renewal, validity options and money back guarantee. Comodo Code Signing Certificate provides infrastructure security for applications using Java, Mozilla Firefox, Apple Mac, Microsoft, etc.
Elements of a code signature:
- Seal- This is a collection of all parts of a code such as identifier, associated files, source, information and more. It is the seal which detects code alterations.
- Digital signature- The seal is signed by a digital signature that includes embedding of this information on all parts of the code. This is also responsible for containing the developer information, validity of the certificate and more.
- Unique identifier- The code can be for anything and thus a system is required to identify what category the code falls into. The identification of a code can be obtained from the seal or from the developer themselves.
When the device browsers search for the code, they come across this signature, which they compare against the original signature of the manufacturer and verify the two. If matched, the browser automatically downloads the controls or codes because of the established trustability. In case the code does not match, it might mean that the code has been tampered with and a warning is displayed on the browser screen to inform the user about the potential threat so that they can decide whether to download or not. However, there is nothing preventing users from downloading the content even if the code signing does not work.
Process of code signing:
- Software manufacturer have to deal with a code sign certificate authority like Symantec or Thawte.
- The developers should ensure that their code is safe to be downloaded and secured from corruption. Signing any code requires a private key that corresponds with a public key and a digital certificate. When the developer acquires the same, they can sign the code of their choice with the company’s credentials.
- A hash mark is created when the digital signature is linked to the code file.
- This hash is decrypted by the device system and either acknowledged or not recognized by the user’s system key. In case the key is verified, the page is opened on the device while in the case of discrepancy either an error is displayed or the code is automatically not downloaded depending on the device settings.
- The steps of running an application can be operated from organizer system or from member center, followed by developer.apple.com by code sign.
Sometimes, there are a certain set of criteria specified by the signer while providing a code signature, which are termed as code requirements. This is written in the technical language and has a script format that includes conditions to be met for the code to be accepted. The process of evaluating whether the signed code meets the requirements is executed only when the operating system needs to determine whether to run a code or not. These can be internal requirements, designated requirement, etc. Obtaining the code sign certificate requires the generation of a private or public key pair as well as documents establishing the identity of the developer. This should be submitted to security companies dealing with issuing certificate who take care of the verification process.
Why should you prefer code signing certificate:
- The first and foremost benefit associated with code signing is establishing the source of the data and the integrity of the manufacturer.
- Having a code signing certificate provides reliability to download increases the number of downloads and maintain reputation of the company.
- It is beneficial because the code signing designs a secure network for software sharing and distributing to users as well as the manufactures.
- Code signing is an effective means to determine whether the code has been tampered intentionally or accidentally by anyone apart from the manufacturer. This provides protection to the data.
- Apple issues this certification process to protect your right as a developer of particular application. It can protect from piracy and malfunction without your acknowledgement. • Signing the code enhances the process of updating the applications for both the users and the makers, as the device system is already familiar with the digital signature and does not require permission.
The iOS operating system installed on Apple phones have been programmed to detect digital code signs before opening content. This makes it necessary for software developers targeting mobile users or people with Apple devices to require a code signing certificate. The decryption process of the code sign requires a root certificate, or determining who has issued the certificate. If a developer has self signed the certificate, it will not hold much value as the systems like iOS might not be familiar with the device operating system. However, if the certificate has been validated with Symantec Code Signing, Thawte Code Signing or Comodo Code Signing the operating system will let the code be downloaded due to established trust policies with these companies.
FIPS-140 Level 2 USB or Existing HSM
Stored on an External Physical Device
3 to 5 Business Days
